No edit summary |
|||
| (5 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
<div class="metadata"> | <div class="metadata"> | ||
<span id="Mateus - Unstable Frequencies"></span> | |||
==Uns(ui)table Frequencies== | ==Uns(ui)table Frequencies== | ||
'''Mateus Domingos''' | '''Mateus Domingos''' | ||
</div> | |||
This workshop was convened around a carefully maintained set of networking and publishing infrastructures. Participating in the workshop we gained a privileged access to these tools, services and system's memory (which constitute a counter model of networked infrastructure). The ServPub server produces an adaptive refiguring of network infrastructure and collective presence. | This workshop was convened around a carefully maintained set of networking and publishing infrastructures. Participating in the workshop we gained a privileged access to these tools, services and system's memory (which constitute a counter model of networked infrastructure). The ServPub server produces an adaptive refiguring of network infrastructure and collective presence. | ||
| Line 25: | Line 27: | ||
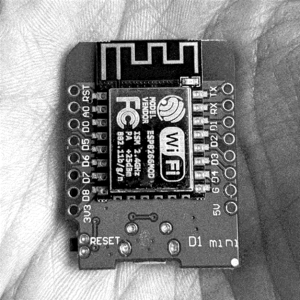
[[File:Wemos D1 Mini Top.png|alt=Wemos D1 Mini microcontroller with ESP8266 chip visible in the centre.|thumb|Wemos D1 Mini topside, ESP8266 chip visible.]] | [[File:Wemos D1 Mini Top.png|alt=Wemos D1 Mini microcontroller with ESP8266 chip visible in the centre.|thumb|Wemos D1 Mini topside, ESP8266 chip visible.]] | ||
< | <noinclude> | ||
[[Category:Content form]] | [[Category:Content form]] | ||
</noinclude> | |||
Latest revision as of 11:19, 7 February 2024
This workshop was convened around a carefully maintained set of networking and publishing infrastructures. Participating in the workshop we gained a privileged access to these tools, services and system's memory (which constitute a counter model of networked infrastructure). The ServPub server produces an adaptive refiguring of network infrastructure and collective presence.
Intending to invite a space for imagination and active participation in these networks, I re-purposed the widely available Wifi-enabled microcontrollers (ESP8266) to introduce a series of local-only Wifi access points, programmed to serve a simple messageboard. My interest in these particular microcontrollers stems from their functionality, offering a low-code entry level into networking devices, that also contains enough flexibility for interesting and surprising uses to emerge. The intent was for these to act as shadow networks to the primary shared server. It was intended to augment our interactions with the server and the collective writing processes. Additionally to these programmed uses it can also hold other interactions that distort the nested protocols.
Visibly, these microcontrollers break the infrastructure into further discrete nodes. More brittle than the wider network, technical capability is traded for limited parameters, that surface protocological moments into active decisions. The reduced component architecture offers some specificity of the material entanglements. We know where the memory is inscribed and under what levels of permanence. We can also follow the combination of manufacturers at least partially involved in this; Espressif, Ai-Thinker, Wemos.
Limiting this shadow network only to the dev-board without additional components or serial communications, the microcontrollers offer useful visual cues as to their possibility; from the visible printed antenna to the sometimes blinking LED. It also opens up the possibility for them to hide ever more discreetly in public spaces.
If part of our exploration of the shared server is understood in relation to conventional methods of digital networking, how does the shared server react to a smaller sibling?
In practice the shadow network remains like weeds growing at the ankles of the ServPub server. To connect to the messageboard or run other services, means disconnecting from the collective spaces of writing on the ServPub server, and the wider internet.
Something that surfaces as an immediate limit is the lack of security offered by the microcontroller. To engage with it in a sustained way requires additional agreements and discussion, emerging from the local context. So it's perhaps always unsuited for activating effective resistance to the dominant form of the internet, but could remain a possible tool for layering upon or around experimental infrastructure, such as the shared server.
It remains a possibility of actions, untaken, and affirming of the practice developed in the shared server. The shadow network follows a Luddite logic of unpicking, allowing space for refusal, the dismissal of certain processes and tools, and the exploration of others, better suited to commonality. It remains open to other passageways of data; a shadow library, a local wiki or static site. When so much is contingent on a connected internet, subject to ever greater modes of extraction, a template of autonomous zones and fragmented protocols appears as a necessary practice.