Systerserver (talk | contribs) (vpn introduction) |
Systerserver (talk | contribs) No edit summary |
||
| (261 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
<blockquote>''"Activist infrastructures are where the messy, grinding, generally invisible labor of 'doing feminism' takes place."'' Cait McKinney in Information Activism - A Queer History of Lesbian Media, 2020<ref>Cait McKinney, ''Information Activism, A Queer History of Lesbian Media Technologies (Duke University Press, 2020)''</ref> | |||
</blockquote> | |||
https:// | == Being part of internets == | ||
[https://systerserver.org Systerserver], a feminist server project of almost two decades,<ref>For more information on the genealogy of Systerserver see Wessalowski, N. & Karagianni, M. “From Feminist Servers to Feminist Federation.” ''A Peer-Reviewed Journal About'' 12, no. 1 (September 7, 2023): 192–208. | |||
from | <nowiki>https://doi.org/10.7146/aprja.v12i1.140450</nowiki>.</ref> has supported the Servpub project with their network infrastructure. The feminists involved in this project have configured their own infrastructure of two physical servers in the data room of [https://esc.mur.at/ <nowiki>[mur.at]</nowiki>], an art association in Graz, Austria, which hosts a wide variety of art and cultural initiatives. The physical servers found this shelter through the networking of activists and artists during [https://eclectictechcarnival.org/ Eclectic Tech Carnival (/ETC]), a self organized skill sharing gathering. Donna Meltzer and Gaba from Systerserver went to Graz to upgrade the servers' hardware in 2019. The first machine, installed and configured in 2005, is called Jean and was refurbished by [https://www.ooooo.be ooooo] in 2023 during their stay in Graz for the Traversal Network of Feminist Servers<ref>Chapter 2: Traveling server space: Why does it matter?, “A Traversal Network of Feminist Servers” 2022. </ref>. The gathering was hosted by [https://esc.mur.at/ ESC], a local media art gallery in Graz, which is affiliated with [mur.at]. | ||
Both servers are running on Debian, which is a Linux based operating system and host several tools for community communications and organising,<ref>Systerserver hosts a GitLab instance as code repository, Peertube for video and streaming, Mailman for mailinglists, Nextcloud for data storage and collective organisation, Mastodon providing a microblogging social networking platform, Tinc VPN, and relevant code based projects and websites. For links to each service, visit https://systerserver.net/</ref> among which Tinc, a virtual private network (VPN) software. The VPN is the most recent addition, facilitating the desire for self hosted servers by our peers, from their homes, studios and spaces that cannot afford a stable digital address.<ref>Configuring a server, requires what is known as a fixed IP address, which is a numeric notation, signaling the location of the server. This IP address can be mapped to a domain name, which in turn can be traceable in the Internet when visiting said domain name in a browser.</ref> Those server projects interweave into a feminist networking, an affective, socio-technical infrastructure, enabling the emergence of more trans-feminist groups and collectives like actinomy (Bremen), leverburns (Amsterdam), caladona (Barcelona), brknhs (Berlin) to host their own servers in their own spaces rather than in data centers, and be reachable through the public internet. | |||
Tinc was chosen as VPN software, mimicking of what Systerserver learnt during their participation in the project A Traversal Network of Feminist Servers (ATNOFS), encountering the mobile server Rosa.<ref>Rosa is rasperry-pi server using, varia.hub to be reachable on the internet. varia hub is what in varia they cal a jumphole, a poetic description for the VPN + reversey proxy through their servers. | |||
Varia is a space for developing collective approaches to everyday technology, work with free software, organise events and collaborate in different constellations. https://varia.zone/en/</ref> Rosa is a server connected to the Internet via a VPN, hosted by the Rotterdam based space Varia, which was inspired by another relevant network infrastructure setup, that of the Rotterdam based institute XPUB.<ref>XPUB is the Master of Arts in Fine Art and Design: Experimental Publishing of the Piet Zwart Institute in Rotterdam. XPUB focuses on the acts of making things public and creating publics in the age of post-digital networks. The VPN software Tinc and reverse proxy is inspired by their HUB project, which enabled the Institute to form an experimental server space for their students which could access the server from outside the Institute, passing institutional firewalls securely and let devices roam. See Docs:03_VPN_with_Tinc</ref> Constant association in Brussels and Hackers and Designers collective in Amsterdam, have also experimented with similar VPN based servers.<ref>Also Mara Karagianni, Michael Murtague and Wendy Van Wynsberghe, were commissioned by Constant for writing a zine manual on Tinc and reverse proxies: Making A Private server Ambulant, https://psaroskalazines.gr/pdf/rosa_beta_25_jan_23.pdf | |||
The beta version of the zine was revisioned and updated by vo ezn, also part of Systerserver. She deployed it in the digital infrastructure of Hackers and Designers.</ref> The people, groups and spaces involved in these servers experiments often overlap, which is also due to the physical proximity of the projects (Rotterdam, Brussels, Amsterdam). | |||
/ | === Being a server === | ||
A VPN software creates virtual private networks, connecting computers and devices that are not sharing the same physical location. In contrast to the internet, the network between these devices is concealed, thus called private, as it only exists between the trusted devices that are added to this network. A VPN can also facilitate a public entry point to these private network connected devices, making them reachable in the public Internet and thus allowing them to become servers. When devices are connected to the Internet, they are assigned a numeric notation, called Internet Protocol (IP) address. A home or office router, is assigned a public IP by its Internet Service Provider (ISP), which changes periodically, so called dynamic. The ISP distributes these IP address from a limited pool of addresses, which expire and trigger an IP address change, so called a lease time, allowing the ISP to provide Internet connection to many more locations than the amount of its IP pool. ISP do this to manage their available addresses more efficiently and for minor security benefits.<ref>IP address lease times provide security benefits such as preventing persistent unauthorized use, reduce risks such as IP spoofing and theft, allow rapid response to misuse by removing compromised devices from the network.</ref> All devices within a home or office, are assigned what is called a local IP from the router, which by its default settings it allows Internet traffic in one way, e.g as websites' content (response), and doesn't allow the devices to send traffic outside the home or the office but only requests. However, within a VPN network, the devices are assigned a private IP by the VPN software, and are able to receive and send traffic outside their physical location. | |||
// --- | [[File:2-what-is-vpn.png|600x600px|center|frameless| Drawing from Tunnel Up/ Tunnel Down zine by Mara Karagianni, introduction about virtual private networks [https://psaroskalazines.gr/pdf/fanzine-VPN-screen-en.pdf]|alt=What is a VPN]] | ||
Visiting a device over the Internet, by remembering their IP, would be a challenging if not impossible thing to do. Thus the need for domain names such as [https://wwww.servpub.net www.servpub.net], which are mapped to an IP address. So when this domain name is visited, the browser can present the content of e.g a website hosted on that device. Retaining this IP the same becomes important for mapping it to a domain name, therefore it's also known as fixed or static IP. The translation of IP to domain names and back, happens with Domain Name Servers or DNS.<ref> A fun guide to what is a DNS, and computer networking in general, it's the zine ''Networking! Ack!'' by Julia Evans, 2017, available at https://jvns.ca/networking-zine.pdf</ref> | |||
[[File:network-hack.png|600x600px|center|frameless|Network! Ack! zine by Julia Evans, introduction about computer networking and how DNS works [https://wizardzines.com/zines/networking/]|alt=Network! Ack!]] | |||
So if a request is made to [https://wiki4print.servpub.net wiki4print.servpub.net], the request will first reach Jean, whose IP is mapped to that domain, because Jean is the only computer with a public and static IP address within this private network. On Jean, a web engine configuration software forwards the request to the private IP of the device, which it actually hosts ServPub project's wiki. The request is thus rerouted internally, meaning inside the concealed virtual private network, to the specific device, which hosts the wiki4print website. This forwarding request from the public IP to the private, is called a proxy request, and the ability of the device to send out data back through the public node, thus being a server, is enabled via a reverse proxy. | |||
Systerserver has configured three of these private networks with Tinc, to reach home based servers which have no public and static IP address: ''internes'', ''alliances'' and ''systerserver''.<ref>The ''internes'' is for Systerserver's machines located in [mur.at] to reach a machine in Antwerp, which is making periodic backups of the servers Jean and Adele. The network ''alliances'' is for facilitating a few of home-based server initiatives within Systerserver's extensive community, such as the etherpad services hosted on the server leverburns which Systerserver uses for technical documentation during server maintenance sessions, or for other allied communities such as caladona and brknhs that want to serve video content without having to commit to the expenses of acquiring a public and static IP address.</ref> The network named ''systerserver'' was the first installation and configuration of Tinc for Systerserver's infrastructure. It was initiated for the publishing infrastructure of the ServPub project. The ''systerserver'' network allows the raspberry-pies, which host the wiki4print and the ServPub website to be accessible in the internet via Systerserver's public node and machine Jean. Arriving to the first technical attempt of configuring the network ''systerserver'' required trust building between Systerserver peers and No Names, which commenced through the participation of Winnie Soon in one of Systerserver's week-long event and workshop in Barcelona back in 2023, during which Systerserver installed PeerTube for and with caladona women's space. Such collective and grassroots organising based events, i messy, campy, the base for bonding and solidarity, which builds upon the invisible labour of doing feminism (McKinney 2020). By understanding together computing, configuring machines, conversing about big tech and its sexism, racial, class and gender discrimination, the people gathered around these events, nourish a resistance through body and identity politics, which transgress labor exchanges on economic value alone.[[File:Protocol_stack_hourglass.jpeg|300x300px|center|frameless|Ip protocol stack]] | |||
== Navigating network politics == | |||
https:// | Looking at the initial architecture of the Internet as a communication medium where a node can reach any other node, and the importance of a node to be authenticated by their address as a unique identifier, the current landscape has transformed to something quite different. Since the end of the 90s the development of the IPv6 protocol was conceived <ref>The first publication of the IPv6 protocol in a Request for Comments was in December 1998, accessed on September 20th, 2025, https://www.rfc-editor.org/rfc/rfc2460.txt</ref> for mitigating the depletion of IPv4 addresses, by enabling larger addresses restoring the initial numeric notation, which hasn't been long enough to cover the massive proliferation of devices. IPv6 was also conceived with embedded security within the IP packet itself. IPv4 required an external configuration of encryption and brought about the development of the encryption protocol IPSec around the mid-1990s, which provided an end-to-end security wrapped around the IP layer, authenticating and encrypting each IP packet. While IPSec ensured encryption for IPv4, it requires extra software installation and configuration steps, but it was incorporated as a core component of IPv6.<ref> Besides IPv6 protocol being a secure protocol with extra authentication and privacy, it also has support for unicast, multicast, anycast. See more at ''Internetworking with TCP/IP'', Vol. 2 by Douglas E. Comer and David L. Stevens, published by Englewood Cliffs, N.J. : Prentice Hall, 1998, accessed on September 20th, 2025, https://archive.org/details/internetworking000come</ref> Therefore, while internet communications over the web, provide encryption with the secure HTTPS certificate,<ref>While HTTPS is a way to secure traffic over the internet, it is distinguished from IPSec in that IPSec secures all data traffic within an IP network, suitable for site-to-site connectivity. HTTPS, the secure version of HTTP, using TLS certificates, secures individual web sessions. The authentication with a TLS certificate relies on the organisation or company's name ownership of the certificate, and not on the integrity of the server's IP address. This fact enables CDNs to cache content and serve in place of the origin server, which contributes to the centralisation of content distribution over the web. https://gcore.com/learning/tls-on-cdn | ||
https:// | |||
More about how TLS works https://www.bacloud.com/en/blog/190/ssl-for-ip-lets-encrypt-now-supports-tlsorssl-certificates-for-ip-addresses.html</ref> other internet connections, e.g files syncing over two machines, require extra encryption configurations and/or VPN tunnels. <!-- add IP auth drawing --> | |||
The use of secure certificates encrypts the traffic over the connection cable and waves, but once the data arrive at their destination server are not encrypted. Thus unencrypted data can be cached and served by intermediaries, which are located closer to users' internet access. E.g when we request again the same website, the content may be served by what is known as Content Distribution Networks (CDNs), rather than the requested server. CDN providers deliver much of today’s Internet content by caching it on servers distributed around the world. By serving data from servers that are geographically close to users, they greatly reduce the impact of physical distance between the user’s Internet access point and the origin server, which in turn speeds up load times. However this centralisation of content, which has been made possible due to digital storage and computing becoming inexpensive since the 2010's, raises several user‑rights concerns despite their performance benefits. Because they terminate secure certificates and have access to unencrypted data, they add an extra point where user data can be inspected, monitored, breached, and their central position also enables large‑scale blocking, filtering and surveillance capitalism that can affect e.g the exercise of erasure, especially when data is moved across borders.<ref>E.g data harvesting and extensive users profiling without consent violates the EU law '''General Data Protection Regulation (GDPR)''', https://wideangle.co/blog/content-delivery-network-cdn-and-gdpr</ref> | |||
The lower motivation for business to offer and maintain both IPv4 and IPv6 network stack, as other technologies such as address-sharing<ref>See for example routing via Network Address Translation (NAT), https://en.wikipedia.org/wiki/Network_address_translation</ref> and CDNs have fixed the issue of handling the scarcity of IP addresses,<ref>Geoff Huston, ''The IPv6 transition'', 2024, accessed on September 20th, 2025 at https://blog.apnic.net/2024/10/22/the-ipv6-transition/</ref> have contributed to a decreased pace in the advancement of IPv6 rollout to all devices. Considering the potential impact of IPv6 where data remain encrypted through out all connections, one may argue whether the embedded encryption within the IPv6 packet for each device on the Internet, it is a civil right to security and privacy that the industry and states' surveillance would rather avoid. At the same time, ISPs can charge higher prices for a reduced number of IPv4 addresses and in some cases, legacy IP blocks of addresses can even be sold in the grey market, because those blocks were not regulated by any regional internet registry system since they were allocated before those registries came to existence.<ref>The African continent registry AFRINIC have been under scrutiny due to organizational and legal problems. In 2019, 4.1 million IPv4 addresses part of unused legacy IP blocks, were sold on the grey market. Accessed online on 25 July 2025 https://en.wikipedia.org/wiki/AFRINIC.</ref> | |||
It is interesting to think of a VPN as a way to render our data unreadable by non-consensual monitoring eyes. In the case of ServPub ambulant server, as a resistance to a university rigid network configuration, besides the wider accessibility and mobility of the server, the content traveling through private networks enforces data encryption and authentication by the VPN software design, and thus becoming unreadable, untraceable and fearless to censorship. What also becomes untraceable is the geolocation of the servers within the private network. | |||
During the translation of Tunnel Up/ Tunnel Down Zine in Chinese,<ref>Tunnel Up/ Tunnel Down, Mara Karagianni, a self-published zine about what is a VPN and its various uses and technologies, 2019, https://psaroskalazines.gr/pdf/fanzine-VPN-screen-en.pdf.</ref> the artist and translator Biyi Wen, referred to the art research project "A Tour of Suspended Handshakes". In this project, artist Cheng Guo physically visits some nodes of China’s Great Firewall. Using network diagnostic tools, the artist identified the geolocations mapped to IP addresses of these critical gateways,<ref>A gateway is a network device that acts as an entry and exit point between two different networks, translating and routing traffic so they can communicate. While a home or office router, mainly forwards packets between networks that use typically IP, a gateway connects different kinds of networks and can translate between differnet protocols or data formats, and often operating across multiple OSI layers.</ref>, which filter data from outside China, based on data published by other researchers. These gateways' function of filtering is what constitutes them as firewalls. At times, the geolocations visited by the artist corresponded to scientific and academic centres, posing like plausible sites for gateway infrastructure. Other times, they lead to desolate locations with no apparent technological presence. While Guo acknowledges that some gateways may be hidden or disguised - for example, antennas camouflaged as lamp posts - the primary reason for these discrepancies lies in the redistribution of IP addresses, due to their resale. These factors make it difficult to pinpoint exact geographical locations. Moreover mapping activities have been illegal in mainland China since 2002, and coordinates remain hidden from the public.<ref>https://en.wikipedia.org/wiki/Restrictions_on_geographic_data_in_China</ref> | |||
In the case of the Great Firewall, the combination of IP redistribution and encrypted coordinates obscures the true geolocations of its gateways, rendering the firewall a nebulous and elusive system. For the mobile (ambulant) servers, their exact geolocation remains obscure too, because they are concealed within the virtual private network -beyond the main public-facing nodes such as Jean-. However, unlike the Great Firewall, the concealment of the ambulant servers is not enforced through a top-down governmental control. The desire to be addressable from home based infrastructures through a trusted network-sharing of tunnels and reverse proxies through community-run servers,<ref>Dynamic DNS is another option for when your ISP changes your home network's IP address.It is a commercial service that allows you also to use a fixed address for your home network. You can often set up DDNS on your router. Self-hosted website or online resource will be redirected over commercial nodes maintained by companies; companies which are often known for data-exploitation, acts of censorship and compliance with states agencies in cases of political prosecution.</ref> brings about the potential to circumvent censorship, surveillance, and centralisation by commercial CDNs, states or other institutional firewalls, rendering this imposed scarcity of IPv4 into a solidarity action. | |||
While writing this chapter, the project of Alison Macrina on Library Freedom Project and Tor Browser was referred to and it is worth mentioning as a concrete, real‑world activist case, reinforcing the "messy, grinding labor of doing feminism". Alison's Library Freedom Project exemplifies this by turning libraries into practical privacy infrastructure sites, teaching surveillance resistance via Tor relays, and anonymise traffic and reclaim data sovereignty, much like Systerserver's VPNs and reverse proxies resist centralised control. | |||
== Digital literacies == | |||
Being part of the internet, or internets,<ref>Networks with an Attitude was a worksession to think of the future of Internet, organised by Constant from 7 to 13 April 2019 at various locations in Antwerp.The internet is dead, long live the internets! https://constantvzw.org/sponge/s/?u=https://www.constantvzw.org/site/-Networks-with-an-Attitude-.html</ref> creating and maintaining our own networked infrastructures involves an understanding of the technicalities and politics of IP addresses, routers and gateways, and the economy of IP scarcity and institutional and corporate control. One way of addressing the politics and economies of network infrastructures and of how to relate to technology is by 'following the data'. Data is not just an informational unit or a technicality, it is how we as trans*feminists relate to computers, both on a supra- or infra-individual level but also as something that can be incredibly personal and intimate. We need to keep asking 'where is the data?'. We need to develop technical awareness and accountability in how we participate and how we are complicit in the infrastructures in which our data is created, stored, sold and analyzed. In 'following the data', we become more engaged and cultivate our sensibilities around data and networked infrastructure politics.<ref>Gray, Jonathan, Carolin Gerlitz, and Liliana Bounegru. “Data Infrastructure Literacy.” ''Big Data & Society'' 5, no. 2 (July 1, 2018) https://journals.sagepub.com/doi/10.1177/2053951718786316</ref> | |||
By making digital infrastructures and technicalities visible with the aid of drawings, diagrams, manuals, metaphors, performances and gatherings, Systerserver traverses technical knowledge with an aim to de-cloud (Hilfling Ritasdatter, Gansing, 2024) data and redistribute networks of machines and humans/species. Systerserver therefore, becomes a space to exchange knowledge, whose sysadmins maintain and care together in non-hierarchical and non-meritocratic ways, which the sysadmins refer to as 'feminist pedagogies'. These pedagogies cultivate a socio-technical learning by accepting divers life experiences, recognising that knowledge is socially constructed, questioning digital hegemonies, and welcoming situated experiences from the places where we physically meet for the trans-feminist gatherings of Eclectic Tech Carnival (/ETC), TransHackFeminist Convergence (THF), or other. These meetings or rather offline and online entanglements are encouraging to Do-It-Together, give time and space to study and collectively write documentation. They collectivize moments of choosing our dependencies, while feeling trusted in a safe(r) place to learn about technicalities. They challenge our bodies-machines relations. | |||
<div id="trans"> | |||
[[File:Root-prepare.jpg|300px|sudo apt upgrade]] | |||
[[File:root-1.jpg|300px|root in public interface anarchaserver]] | |||
[[File:Port443-ssl.jpg|300px|port 443]] | |||
''How can we imagine a virtual private server, in a material world?'' An intervention by ooooo and others during the rehabilitation of an eco-industrial colony in the mountains near Barcelona, Calafou, a room was transformed into a physical public interface for the practices around the feminist server: anarchaserver.org<ref>The documentation of this process https://zoiahorn.anarchaserver.org/physical-process/ is hosted on the anarchaserver. Anarchaserver is an allied feminist server which contributes to the maintenance of autonomous infrastructure on the Internet for feminists projects and was setup in Calafou, Spain.</ref> Open for visitors, it was used during system administrative work sessions, and for gatherings, sonic improvisations and radio. The door, window, ceilings and multi-levels were analogous to the functionalities of a server’s hardware-software counterparts (ports, encryption, including a repository, and even a firewall). It also had a bed, where somebody could sleep, rest and reside in analogy with the Living Data container, which hosts [https://alexandria.anarchaserver.org/index.php/Main_Page ALEXANDRIA] for wiki documenting and [https://zoiahorn.anarchaserver.org/ ZOIA HORN] for multi-site blogging. It was also activated during THF Convergence, an event of intersectional feminists, queer and trans people of all genders to better understand, use and ultimately develop free and liberating technologies for social dissent. | |||
</div> | |||
<div id="trans"> | |||
[[File:Server-wiki-act5.png|600px|Sever - wiki - act5]] | |||
With the question ''How to collectively embody a server?'' ooooo made another performative event during The Feminist Server Summit, 12–15 December 2013<ref>The fourteenth edition of the meeting days Verbindingen/Jonctions organized by constant vzw in December 2013 was dedicated to a Feminist review of mesh, cloud, autonomous, and DIY servers. https://areyoubeingserved.constantvzw.org/Summit.xhtml</ref>, organized by Constant association of media arts in Brussels. In ''Home is a server'' fourteen people were invited to choose a prop representing the different hardware parts of a computer (CPU, RAM, watchdogs, ports, kernels, hard drives). By reading a script together, they followed the data flow while installing a server, install a wiki and publish a recipe for pancakes which they bake and eat together. | |||
< | </div> | ||
[[ | |||
</ | <div id="trans"> | ||
[[File:Cryptodance.png|600px|Cryptodance]] | |||
''Are we vulnerable, safe and do we need to encrypt?'' In different exercises combining dance notations, crypto techniques and careful somatic tactics participants embody issues of security, privacy, safety and surveillance. ''Cryptodance'' was a performative event which was developed in August 2016 during the preparations for [https://femhack.noblogs.org/post/2016/05/31/thf2016-en/ THF 2016!], by a small international constellation of choreographers, hackers and dancers. <ref>Goldjian and bolwerK started plotting the Cryptodance project during a Ministry of Hacking (hosted by esc in Graz, Austria), where they formed a joint(ad)venture of the Department of Waves and Shadow and the Department of Care and Wonder.Cryptodance - THF 2016</ref> | |||
</div> | |||
<div id="trans"> | |||
[[File:File-silkscreen-final.jpg|alt=Diffie-Hellman|center|thumb|Diffie-Hellman drawing by Mara Karagianni (Systerserver)]] | |||
''Crypto Keys'' is a drawing illustrating the mathematical formulas used in the Diffie Hellman algorithm for encrypting data over the Internet without the need to exchange the password or secret key. | |||
</div> | |||
<div id="trans"> | |||
[[File:Bundle-vpn-zines.jpg|alt=VPN zines|center|thumb|VPN zines by Mara Karagianni (Systerserver)]] | |||
''VPN introduction zines'' is a series of manuals about private virtual networks illustrating with drawings technical concepts of firewalls, authentication and encryption over the Internet'','' how we can install a VPN with a single board computer, on mobile phones, and when to chose for a VPN over a proxy. | |||
</div> | |||
<div id="trans"> | |||
[[File:hummingbird.png|600px|Humming Birds]] | |||
''What is feminist federation?'' Another example of making analogies and tangible translations, it the performative event ''Humming Birds''. With the aid of choreographies, sociometric exercises and voicing techniques, participants explore the social network Fediverse and get introduced in a technical understanding of its protocol ActivityPub, which is a standard for publishing content in a decentralized social networking.<ref>Nate Wessalowski and xm developed it during 360 degrees of proximities for the cyborg collective of Caladona, a women center in Barcelona with whom they together installed peertube on a self-hosted server. ActivityPub provides a client-to-server API for creating and modifying content, as well as a federated server-to-server protocol for delivering notifications and content to other servers.</ref> | |||
</div> | |||
== A feminist networking == | |||
<blockquote> | |||
''"Technologies are about relations with things we would like to relate to, but also things we'' ''don't want to be related to"'' Femke Snelting in Forms of Ongoingness, 2018<ref>Sollfrank, C."Forms of Ongoingness. Interview with Femke Snelting and spideralex". House for Electronic Arts (HeK), Basel. (September18, 2018) https://creatingcommons.zhdk.ch/wp-content/uploads/2020/06/Transcript-Femkespider.pdf</ref></blockquote> | |||
A feminist server goes beyond a technically facilitated node in the network, and becomes an (online) space in understanding digital infrastructures and resist hegemonies. It can be entered "as an inhabitant, to which we make contributions, nurture a safe space and a place for expression and experimentation, a place for taking a role in hacking heteronormativity and patriarchy."<ref>spideralex in Sollfrank, C."Forms of Ongoingness. Interview with Femke Snelting and spideralex". House for Electronic Arts (HeK), Basel. (September18, 2018) https://creatingcommons.zhdk.ch/wp-content/uploads/2020/06/Transcript-Femkespider.pdf</ref> A feminist server is a place where we as trans*feminists can share with intersectional, queer and feminist communities, a place where our data and the contents of our websites are hosted, where we are chatting, storing stories and imaginaries, and accessing the tools we need to get organized (mailing lists, calendars, etherpads). Serving, and becoming a server is not just a neutral relation between two or more computers.<ref>Gargaglione, E. “Hacking Maintenance With Care Reflections on the Self-administered Survival of Digital Solidarity Networks". Roots§Routes. (May 14, 2023). | |||
https://www.roots-routes.org/hacking-maintenance-with-care-reflections-on-the-self-administered-survival-of-digital-solidarity-networks-by-erica-gargaglione/ [client/server nor user/developper]</ref> It is tied to politics of protocols, of infrastructure capacity and power, responsibilities, dependencies, invisible labour, knowledge, and control. A feminist server is a space where we learn how a collective emancipation is possible from the techno-fascist platforms and content service providers. As feminist servers, we refuse to be served in networks that increase our dependencies on cis male dominated and extractivist technologies of big tech. Having a place or 'a room of one's own' on the internet is therefore important, referencing historic feminist struggles for agency, and safe/r off- and online spaces for uninterrupted time together to imagine technological praxis otherwise. | |||
Furthermore, the metaphor of one's own room<ref>Networks Of One’s Own is a periodic para-nodal publication by varia. September 2019. <nowiki>https://networksofonesown.varia.zone/</nowiki></ref> highlights the ways in which bodies need to be accommodated in the practices of feminist servers and social networking. These bodies incorporate our data bodies<ref>Association for Progressive Communications.: Peña, P and Varon,J. “Consent to Our Data Bodies: Lessons From Feminist Theories to Enforce Data Protection,” oding Rights (March 25, 2019). | |||
https://www.apc.org/en/pubs/consent-our-data-bodies-lessons-feminist-theories-enforce-data-protection</ref> but also the ways in which we show up in gatherings and places outside the digital networks. Self-organised gatherings such as the [https://eclectictechcarnival.org Eclectic Tech Carnival] (/ETC)<ref>The '''Eclectic Tech Carnival''' (/ETC) is a potent gathering of feminists who critically explore and develop everyday skills and information technologies in the context of free software and open hardware. /ETC chews on the roots of control and domination, disrupts patriarchal societies and imagines better alternatives. https://monoskop.org/Eclectic_Tech_Carnival</ref> or the TransHackFeminist convergence (THF),<ref>https://alexandria.anarchaserver.org/index.php/Main_Page#TransHackFeminist_Convergence</ref> and feminist hacklabs such as [https://www.marialab.org/ marialab], [https://www.fluidspace.org fluid.space], [https://www.mzbaltazarslaboratory.org/ mz balathazar’s laboratory], [https://wiki.digitalcare.noho.st/ t_cyberhol], as well as (art) residencies or other larger gatherings (Global Gathering, Privacycamp, OFFDEM, CCC) have been crucially nurturing and fueling the desires for our own servers. These gatherings address the need to share ways of doing, tools and strategies to overcome and overthrow the monocultural, centralised oligopolic technologies of surveillance and control, to resist the matrix of domination. These are moments where social networking can materialize into feminist servers and affective infrastructures.<ref>Wessalowski, N. & Karagianni, M. “From Feminist Servers to Feminist Federation.” ''A Peer-Reviewed Journal About'' 12, no. 1 (September 7, 2023): 192–208. | |||
https://doi.org/10.7146/aprja.v12i1.140450</ref> | |||
Social networking, which shapes affective infrastructures, can be in that sense laborious, an act of care, of wielding solidarities, of sharing and of growing alliances, recognizing our precarities, identities and collective oppressions. It is a community practice, a way of staying connected and connecting anew, of looking for and cherishing those critical connections<ref>Following a quote from Grace Lee Hoggs on connectedness and activism which puts 'critical connections' over 'critical mass' after an idea by Margaret Wheatly. | |||
Boggs, G., Kurashige, S. ''The Next American Revolution: Sustainable Activism for the Twenty-First Century''. Univ of California Press, 2012. p.50)</ref> which are always already more than technical. Those critical connections can become a feminist networking, a situated techno-political practice that engages us in more-than-human relations with hardware, wetware and software. | |||
In terms of feminist servers, the server thus becomes a 'connected room' or even 'infrastructures of one's own', characterized by the tension between the need for self-determination and the promiscuous and contagious practices of networking and making contact with others. These practices inherently surpass strong notions of the individual 'self', facilitating instead a collective and heterogeneous search for empowerment, and partake in creating the conditions for networked subjectivities and solidarities. They transform to a connected room,<ref>See also spideralex, referencing Remedios Zafra's book "A Connected Room of One’s Own" https://www.remedioszafra.net/aconnectedroom.html in Sollfrank, C."Forms of Ongoingness. Interview with Femke Snelting and spideralex". House for Electronic Arts (HeK), Basel. (September18, 2018) https://creatingcommons.zhdk.ch/wp-content/uploads/2020/06/Transcript-Femkespider.pdf</ref> a network of one's own, with allies as co-dependencies, attributing each other(s), interacting as radical references<ref>Term introduced in this book by ooooo, which got picked up an lead to an in depth article on the subject in [https://wiki4print.servpub.net/index.php?title=Chapter_5b:_Distribution Chapter_5b:_Distribution]</ref> to evade hierarchies of cultural capital, and instead sustain collective efforts of resistance against capitalistic logics of knowledge production. When one is talking about the internet and its potential for feminist networking, one needs to move away from thinking of it as something 'given' that we might 'use'. One needs to shift away from the cloudy image of cyberspace serving the extension and intensification of capital, governance and data power.<ref>Metahaven, Daniel van der Velden, and Vinca Kruk. 2012. ‘Captives of the Cloud: Part I’. ''E-Flux'' 37.</ref> | |||
''ServPub, being a publishing platform for collaboration, learning digital infrastructuring while doing it, and being part of Systerserver's internet and networking, is moving toward feminist forms of affective infrastructures.'' | |||
----<!-- this is just comment on. ref: | |||
item 9: spelling on projekt? or project? | |||
item 11: when? | |||
item 13: lack year or link | |||
item 19: need full ref | |||
item 7: rework on the ref? | |||
--><references /> | |||
Latest revision as of 18:24, 10 January 2026
"Activist infrastructures are where the messy, grinding, generally invisible labor of 'doing feminism' takes place." Cait McKinney in Information Activism - A Queer History of Lesbian Media, 2020[1]
Being part of internets
Systerserver, a feminist server project of almost two decades,[2] has supported the Servpub project with their network infrastructure. The feminists involved in this project have configured their own infrastructure of two physical servers in the data room of [mur.at], an art association in Graz, Austria, which hosts a wide variety of art and cultural initiatives. The physical servers found this shelter through the networking of activists and artists during Eclectic Tech Carnival (/ETC), a self organized skill sharing gathering. Donna Meltzer and Gaba from Systerserver went to Graz to upgrade the servers' hardware in 2019. The first machine, installed and configured in 2005, is called Jean and was refurbished by ooooo in 2023 during their stay in Graz for the Traversal Network of Feminist Servers[3]. The gathering was hosted by ESC, a local media art gallery in Graz, which is affiliated with [mur.at].
Both servers are running on Debian, which is a Linux based operating system and host several tools for community communications and organising,[4] among which Tinc, a virtual private network (VPN) software. The VPN is the most recent addition, facilitating the desire for self hosted servers by our peers, from their homes, studios and spaces that cannot afford a stable digital address.[5] Those server projects interweave into a feminist networking, an affective, socio-technical infrastructure, enabling the emergence of more trans-feminist groups and collectives like actinomy (Bremen), leverburns (Amsterdam), caladona (Barcelona), brknhs (Berlin) to host their own servers in their own spaces rather than in data centers, and be reachable through the public internet.
Tinc was chosen as VPN software, mimicking of what Systerserver learnt during their participation in the project A Traversal Network of Feminist Servers (ATNOFS), encountering the mobile server Rosa.[6] Rosa is a server connected to the Internet via a VPN, hosted by the Rotterdam based space Varia, which was inspired by another relevant network infrastructure setup, that of the Rotterdam based institute XPUB.[7] Constant association in Brussels and Hackers and Designers collective in Amsterdam, have also experimented with similar VPN based servers.[8] The people, groups and spaces involved in these servers experiments often overlap, which is also due to the physical proximity of the projects (Rotterdam, Brussels, Amsterdam).
Being a server
A VPN software creates virtual private networks, connecting computers and devices that are not sharing the same physical location. In contrast to the internet, the network between these devices is concealed, thus called private, as it only exists between the trusted devices that are added to this network. A VPN can also facilitate a public entry point to these private network connected devices, making them reachable in the public Internet and thus allowing them to become servers. When devices are connected to the Internet, they are assigned a numeric notation, called Internet Protocol (IP) address. A home or office router, is assigned a public IP by its Internet Service Provider (ISP), which changes periodically, so called dynamic. The ISP distributes these IP address from a limited pool of addresses, which expire and trigger an IP address change, so called a lease time, allowing the ISP to provide Internet connection to many more locations than the amount of its IP pool. ISP do this to manage their available addresses more efficiently and for minor security benefits.[9] All devices within a home or office, are assigned what is called a local IP from the router, which by its default settings it allows Internet traffic in one way, e.g as websites' content (response), and doesn't allow the devices to send traffic outside the home or the office but only requests. However, within a VPN network, the devices are assigned a private IP by the VPN software, and are able to receive and send traffic outside their physical location.
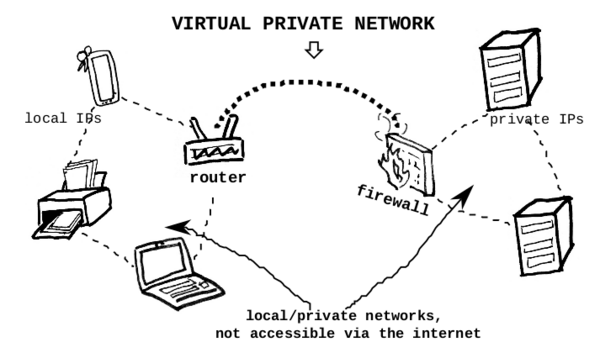
Visiting a device over the Internet, by remembering their IP, would be a challenging if not impossible thing to do. Thus the need for domain names such as www.servpub.net, which are mapped to an IP address. So when this domain name is visited, the browser can present the content of e.g a website hosted on that device. Retaining this IP the same becomes important for mapping it to a domain name, therefore it's also known as fixed or static IP. The translation of IP to domain names and back, happens with Domain Name Servers or DNS.[10]

So if a request is made to wiki4print.servpub.net, the request will first reach Jean, whose IP is mapped to that domain, because Jean is the only computer with a public and static IP address within this private network. On Jean, a web engine configuration software forwards the request to the private IP of the device, which it actually hosts ServPub project's wiki. The request is thus rerouted internally, meaning inside the concealed virtual private network, to the specific device, which hosts the wiki4print website. This forwarding request from the public IP to the private, is called a proxy request, and the ability of the device to send out data back through the public node, thus being a server, is enabled via a reverse proxy.
Systerserver has configured three of these private networks with Tinc, to reach home based servers which have no public and static IP address: internes, alliances and systerserver.[11] The network named systerserver was the first installation and configuration of Tinc for Systerserver's infrastructure. It was initiated for the publishing infrastructure of the ServPub project. The systerserver network allows the raspberry-pies, which host the wiki4print and the ServPub website to be accessible in the internet via Systerserver's public node and machine Jean. Arriving to the first technical attempt of configuring the network systerserver required trust building between Systerserver peers and No Names, which commenced through the participation of Winnie Soon in one of Systerserver's week-long event and workshop in Barcelona back in 2023, during which Systerserver installed PeerTube for and with caladona women's space. Such collective and grassroots organising based events, i messy, campy, the base for bonding and solidarity, which builds upon the invisible labour of doing feminism (McKinney 2020). By understanding together computing, configuring machines, conversing about big tech and its sexism, racial, class and gender discrimination, the people gathered around these events, nourish a resistance through body and identity politics, which transgress labor exchanges on economic value alone.
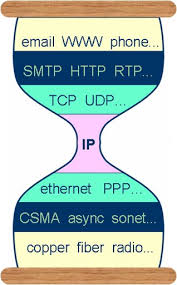
Looking at the initial architecture of the Internet as a communication medium where a node can reach any other node, and the importance of a node to be authenticated by their address as a unique identifier, the current landscape has transformed to something quite different. Since the end of the 90s the development of the IPv6 protocol was conceived [12] for mitigating the depletion of IPv4 addresses, by enabling larger addresses restoring the initial numeric notation, which hasn't been long enough to cover the massive proliferation of devices. IPv6 was also conceived with embedded security within the IP packet itself. IPv4 required an external configuration of encryption and brought about the development of the encryption protocol IPSec around the mid-1990s, which provided an end-to-end security wrapped around the IP layer, authenticating and encrypting each IP packet. While IPSec ensured encryption for IPv4, it requires extra software installation and configuration steps, but it was incorporated as a core component of IPv6.[13] Therefore, while internet communications over the web, provide encryption with the secure HTTPS certificate,[14] other internet connections, e.g files syncing over two machines, require extra encryption configurations and/or VPN tunnels.
The use of secure certificates encrypts the traffic over the connection cable and waves, but once the data arrive at their destination server are not encrypted. Thus unencrypted data can be cached and served by intermediaries, which are located closer to users' internet access. E.g when we request again the same website, the content may be served by what is known as Content Distribution Networks (CDNs), rather than the requested server. CDN providers deliver much of today’s Internet content by caching it on servers distributed around the world. By serving data from servers that are geographically close to users, they greatly reduce the impact of physical distance between the user’s Internet access point and the origin server, which in turn speeds up load times. However this centralisation of content, which has been made possible due to digital storage and computing becoming inexpensive since the 2010's, raises several user‑rights concerns despite their performance benefits. Because they terminate secure certificates and have access to unencrypted data, they add an extra point where user data can be inspected, monitored, breached, and their central position also enables large‑scale blocking, filtering and surveillance capitalism that can affect e.g the exercise of erasure, especially when data is moved across borders.[15]
The lower motivation for business to offer and maintain both IPv4 and IPv6 network stack, as other technologies such as address-sharing[16] and CDNs have fixed the issue of handling the scarcity of IP addresses,[17] have contributed to a decreased pace in the advancement of IPv6 rollout to all devices. Considering the potential impact of IPv6 where data remain encrypted through out all connections, one may argue whether the embedded encryption within the IPv6 packet for each device on the Internet, it is a civil right to security and privacy that the industry and states' surveillance would rather avoid. At the same time, ISPs can charge higher prices for a reduced number of IPv4 addresses and in some cases, legacy IP blocks of addresses can even be sold in the grey market, because those blocks were not regulated by any regional internet registry system since they were allocated before those registries came to existence.[18]
It is interesting to think of a VPN as a way to render our data unreadable by non-consensual monitoring eyes. In the case of ServPub ambulant server, as a resistance to a university rigid network configuration, besides the wider accessibility and mobility of the server, the content traveling through private networks enforces data encryption and authentication by the VPN software design, and thus becoming unreadable, untraceable and fearless to censorship. What also becomes untraceable is the geolocation of the servers within the private network.
During the translation of Tunnel Up/ Tunnel Down Zine in Chinese,[19] the artist and translator Biyi Wen, referred to the art research project "A Tour of Suspended Handshakes". In this project, artist Cheng Guo physically visits some nodes of China’s Great Firewall. Using network diagnostic tools, the artist identified the geolocations mapped to IP addresses of these critical gateways,[20], which filter data from outside China, based on data published by other researchers. These gateways' function of filtering is what constitutes them as firewalls. At times, the geolocations visited by the artist corresponded to scientific and academic centres, posing like plausible sites for gateway infrastructure. Other times, they lead to desolate locations with no apparent technological presence. While Guo acknowledges that some gateways may be hidden or disguised - for example, antennas camouflaged as lamp posts - the primary reason for these discrepancies lies in the redistribution of IP addresses, due to their resale. These factors make it difficult to pinpoint exact geographical locations. Moreover mapping activities have been illegal in mainland China since 2002, and coordinates remain hidden from the public.[21]
In the case of the Great Firewall, the combination of IP redistribution and encrypted coordinates obscures the true geolocations of its gateways, rendering the firewall a nebulous and elusive system. For the mobile (ambulant) servers, their exact geolocation remains obscure too, because they are concealed within the virtual private network -beyond the main public-facing nodes such as Jean-. However, unlike the Great Firewall, the concealment of the ambulant servers is not enforced through a top-down governmental control. The desire to be addressable from home based infrastructures through a trusted network-sharing of tunnels and reverse proxies through community-run servers,[22] brings about the potential to circumvent censorship, surveillance, and centralisation by commercial CDNs, states or other institutional firewalls, rendering this imposed scarcity of IPv4 into a solidarity action.
While writing this chapter, the project of Alison Macrina on Library Freedom Project and Tor Browser was referred to and it is worth mentioning as a concrete, real‑world activist case, reinforcing the "messy, grinding labor of doing feminism". Alison's Library Freedom Project exemplifies this by turning libraries into practical privacy infrastructure sites, teaching surveillance resistance via Tor relays, and anonymise traffic and reclaim data sovereignty, much like Systerserver's VPNs and reverse proxies resist centralised control.
Digital literacies
Being part of the internet, or internets,[23] creating and maintaining our own networked infrastructures involves an understanding of the technicalities and politics of IP addresses, routers and gateways, and the economy of IP scarcity and institutional and corporate control. One way of addressing the politics and economies of network infrastructures and of how to relate to technology is by 'following the data'. Data is not just an informational unit or a technicality, it is how we as trans*feminists relate to computers, both on a supra- or infra-individual level but also as something that can be incredibly personal and intimate. We need to keep asking 'where is the data?'. We need to develop technical awareness and accountability in how we participate and how we are complicit in the infrastructures in which our data is created, stored, sold and analyzed. In 'following the data', we become more engaged and cultivate our sensibilities around data and networked infrastructure politics.[24]
By making digital infrastructures and technicalities visible with the aid of drawings, diagrams, manuals, metaphors, performances and gatherings, Systerserver traverses technical knowledge with an aim to de-cloud (Hilfling Ritasdatter, Gansing, 2024) data and redistribute networks of machines and humans/species. Systerserver therefore, becomes a space to exchange knowledge, whose sysadmins maintain and care together in non-hierarchical and non-meritocratic ways, which the sysadmins refer to as 'feminist pedagogies'. These pedagogies cultivate a socio-technical learning by accepting divers life experiences, recognising that knowledge is socially constructed, questioning digital hegemonies, and welcoming situated experiences from the places where we physically meet for the trans-feminist gatherings of Eclectic Tech Carnival (/ETC), TransHackFeminist Convergence (THF), or other. These meetings or rather offline and online entanglements are encouraging to Do-It-Together, give time and space to study and collectively write documentation. They collectivize moments of choosing our dependencies, while feeling trusted in a safe(r) place to learn about technicalities. They challenge our bodies-machines relations.
How can we imagine a virtual private server, in a material world? An intervention by ooooo and others during the rehabilitation of an eco-industrial colony in the mountains near Barcelona, Calafou, a room was transformed into a physical public interface for the practices around the feminist server: anarchaserver.org[25] Open for visitors, it was used during system administrative work sessions, and for gatherings, sonic improvisations and radio. The door, window, ceilings and multi-levels were analogous to the functionalities of a server’s hardware-software counterparts (ports, encryption, including a repository, and even a firewall). It also had a bed, where somebody could sleep, rest and reside in analogy with the Living Data container, which hosts ALEXANDRIA for wiki documenting and ZOIA HORN for multi-site blogging. It was also activated during THF Convergence, an event of intersectional feminists, queer and trans people of all genders to better understand, use and ultimately develop free and liberating technologies for social dissent.
With the question How to collectively embody a server? ooooo made another performative event during The Feminist Server Summit, 12–15 December 2013[26], organized by Constant association of media arts in Brussels. In Home is a server fourteen people were invited to choose a prop representing the different hardware parts of a computer (CPU, RAM, watchdogs, ports, kernels, hard drives). By reading a script together, they followed the data flow while installing a server, install a wiki and publish a recipe for pancakes which they bake and eat together.
Are we vulnerable, safe and do we need to encrypt? In different exercises combining dance notations, crypto techniques and careful somatic tactics participants embody issues of security, privacy, safety and surveillance. Cryptodance was a performative event which was developed in August 2016 during the preparations for THF 2016!, by a small international constellation of choreographers, hackers and dancers. [27]
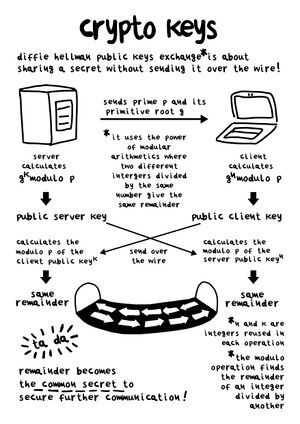
Crypto Keys is a drawing illustrating the mathematical formulas used in the Diffie Hellman algorithm for encrypting data over the Internet without the need to exchange the password or secret key.

VPN introduction zines is a series of manuals about private virtual networks illustrating with drawings technical concepts of firewalls, authentication and encryption over the Internet, how we can install a VPN with a single board computer, on mobile phones, and when to chose for a VPN over a proxy.
What is feminist federation? Another example of making analogies and tangible translations, it the performative event Humming Birds. With the aid of choreographies, sociometric exercises and voicing techniques, participants explore the social network Fediverse and get introduced in a technical understanding of its protocol ActivityPub, which is a standard for publishing content in a decentralized social networking.[28]
A feminist networking
"Technologies are about relations with things we would like to relate to, but also things we don't want to be related to" Femke Snelting in Forms of Ongoingness, 2018[29]
A feminist server goes beyond a technically facilitated node in the network, and becomes an (online) space in understanding digital infrastructures and resist hegemonies. It can be entered "as an inhabitant, to which we make contributions, nurture a safe space and a place for expression and experimentation, a place for taking a role in hacking heteronormativity and patriarchy."[30] A feminist server is a place where we as trans*feminists can share with intersectional, queer and feminist communities, a place where our data and the contents of our websites are hosted, where we are chatting, storing stories and imaginaries, and accessing the tools we need to get organized (mailing lists, calendars, etherpads). Serving, and becoming a server is not just a neutral relation between two or more computers.[31] It is tied to politics of protocols, of infrastructure capacity and power, responsibilities, dependencies, invisible labour, knowledge, and control. A feminist server is a space where we learn how a collective emancipation is possible from the techno-fascist platforms and content service providers. As feminist servers, we refuse to be served in networks that increase our dependencies on cis male dominated and extractivist technologies of big tech. Having a place or 'a room of one's own' on the internet is therefore important, referencing historic feminist struggles for agency, and safe/r off- and online spaces for uninterrupted time together to imagine technological praxis otherwise.
Furthermore, the metaphor of one's own room[32] highlights the ways in which bodies need to be accommodated in the practices of feminist servers and social networking. These bodies incorporate our data bodies[33] but also the ways in which we show up in gatherings and places outside the digital networks. Self-organised gatherings such as the Eclectic Tech Carnival (/ETC)[34] or the TransHackFeminist convergence (THF),[35] and feminist hacklabs such as marialab, fluid.space, mz balathazar’s laboratory, t_cyberhol, as well as (art) residencies or other larger gatherings (Global Gathering, Privacycamp, OFFDEM, CCC) have been crucially nurturing and fueling the desires for our own servers. These gatherings address the need to share ways of doing, tools and strategies to overcome and overthrow the monocultural, centralised oligopolic technologies of surveillance and control, to resist the matrix of domination. These are moments where social networking can materialize into feminist servers and affective infrastructures.[36]
Social networking, which shapes affective infrastructures, can be in that sense laborious, an act of care, of wielding solidarities, of sharing and of growing alliances, recognizing our precarities, identities and collective oppressions. It is a community practice, a way of staying connected and connecting anew, of looking for and cherishing those critical connections[37] which are always already more than technical. Those critical connections can become a feminist networking, a situated techno-political practice that engages us in more-than-human relations with hardware, wetware and software.
In terms of feminist servers, the server thus becomes a 'connected room' or even 'infrastructures of one's own', characterized by the tension between the need for self-determination and the promiscuous and contagious practices of networking and making contact with others. These practices inherently surpass strong notions of the individual 'self', facilitating instead a collective and heterogeneous search for empowerment, and partake in creating the conditions for networked subjectivities and solidarities. They transform to a connected room,[38] a network of one's own, with allies as co-dependencies, attributing each other(s), interacting as radical references[39] to evade hierarchies of cultural capital, and instead sustain collective efforts of resistance against capitalistic logics of knowledge production. When one is talking about the internet and its potential for feminist networking, one needs to move away from thinking of it as something 'given' that we might 'use'. One needs to shift away from the cloudy image of cyberspace serving the extension and intensification of capital, governance and data power.[40]
ServPub, being a publishing platform for collaboration, learning digital infrastructuring while doing it, and being part of Systerserver's internet and networking, is moving toward feminist forms of affective infrastructures.
- ↑ Cait McKinney, Information Activism, A Queer History of Lesbian Media Technologies (Duke University Press, 2020)
- ↑ For more information on the genealogy of Systerserver see Wessalowski, N. & Karagianni, M. “From Feminist Servers to Feminist Federation.” A Peer-Reviewed Journal About 12, no. 1 (September 7, 2023): 192–208. https://doi.org/10.7146/aprja.v12i1.140450.
- ↑ Chapter 2: Traveling server space: Why does it matter?, “A Traversal Network of Feminist Servers” 2022.
- ↑ Systerserver hosts a GitLab instance as code repository, Peertube for video and streaming, Mailman for mailinglists, Nextcloud for data storage and collective organisation, Mastodon providing a microblogging social networking platform, Tinc VPN, and relevant code based projects and websites. For links to each service, visit https://systerserver.net/
- ↑ Configuring a server, requires what is known as a fixed IP address, which is a numeric notation, signaling the location of the server. This IP address can be mapped to a domain name, which in turn can be traceable in the Internet when visiting said domain name in a browser.
- ↑ Rosa is rasperry-pi server using, varia.hub to be reachable on the internet. varia hub is what in varia they cal a jumphole, a poetic description for the VPN + reversey proxy through their servers. Varia is a space for developing collective approaches to everyday technology, work with free software, organise events and collaborate in different constellations. https://varia.zone/en/
- ↑ XPUB is the Master of Arts in Fine Art and Design: Experimental Publishing of the Piet Zwart Institute in Rotterdam. XPUB focuses on the acts of making things public and creating publics in the age of post-digital networks. The VPN software Tinc and reverse proxy is inspired by their HUB project, which enabled the Institute to form an experimental server space for their students which could access the server from outside the Institute, passing institutional firewalls securely and let devices roam. See Docs:03_VPN_with_Tinc
- ↑ Also Mara Karagianni, Michael Murtague and Wendy Van Wynsberghe, were commissioned by Constant for writing a zine manual on Tinc and reverse proxies: Making A Private server Ambulant, https://psaroskalazines.gr/pdf/rosa_beta_25_jan_23.pdf The beta version of the zine was revisioned and updated by vo ezn, also part of Systerserver. She deployed it in the digital infrastructure of Hackers and Designers.
- ↑ IP address lease times provide security benefits such as preventing persistent unauthorized use, reduce risks such as IP spoofing and theft, allow rapid response to misuse by removing compromised devices from the network.
- ↑ A fun guide to what is a DNS, and computer networking in general, it's the zine Networking! Ack! by Julia Evans, 2017, available at https://jvns.ca/networking-zine.pdf
- ↑ The internes is for Systerserver's machines located in [mur.at] to reach a machine in Antwerp, which is making periodic backups of the servers Jean and Adele. The network alliances is for facilitating a few of home-based server initiatives within Systerserver's extensive community, such as the etherpad services hosted on the server leverburns which Systerserver uses for technical documentation during server maintenance sessions, or for other allied communities such as caladona and brknhs that want to serve video content without having to commit to the expenses of acquiring a public and static IP address.
- ↑ The first publication of the IPv6 protocol in a Request for Comments was in December 1998, accessed on September 20th, 2025, https://www.rfc-editor.org/rfc/rfc2460.txt
- ↑ Besides IPv6 protocol being a secure protocol with extra authentication and privacy, it also has support for unicast, multicast, anycast. See more at Internetworking with TCP/IP, Vol. 2 by Douglas E. Comer and David L. Stevens, published by Englewood Cliffs, N.J. : Prentice Hall, 1998, accessed on September 20th, 2025, https://archive.org/details/internetworking000come
- ↑ While HTTPS is a way to secure traffic over the internet, it is distinguished from IPSec in that IPSec secures all data traffic within an IP network, suitable for site-to-site connectivity. HTTPS, the secure version of HTTP, using TLS certificates, secures individual web sessions. The authentication with a TLS certificate relies on the organisation or company's name ownership of the certificate, and not on the integrity of the server's IP address. This fact enables CDNs to cache content and serve in place of the origin server, which contributes to the centralisation of content distribution over the web. https://gcore.com/learning/tls-on-cdn More about how TLS works https://www.bacloud.com/en/blog/190/ssl-for-ip-lets-encrypt-now-supports-tlsorssl-certificates-for-ip-addresses.html
- ↑ E.g data harvesting and extensive users profiling without consent violates the EU law General Data Protection Regulation (GDPR), https://wideangle.co/blog/content-delivery-network-cdn-and-gdpr
- ↑ See for example routing via Network Address Translation (NAT), https://en.wikipedia.org/wiki/Network_address_translation
- ↑ Geoff Huston, The IPv6 transition, 2024, accessed on September 20th, 2025 at https://blog.apnic.net/2024/10/22/the-ipv6-transition/
- ↑ The African continent registry AFRINIC have been under scrutiny due to organizational and legal problems. In 2019, 4.1 million IPv4 addresses part of unused legacy IP blocks, were sold on the grey market. Accessed online on 25 July 2025 https://en.wikipedia.org/wiki/AFRINIC.
- ↑ Tunnel Up/ Tunnel Down, Mara Karagianni, a self-published zine about what is a VPN and its various uses and technologies, 2019, https://psaroskalazines.gr/pdf/fanzine-VPN-screen-en.pdf.
- ↑ A gateway is a network device that acts as an entry and exit point between two different networks, translating and routing traffic so they can communicate. While a home or office router, mainly forwards packets between networks that use typically IP, a gateway connects different kinds of networks and can translate between differnet protocols or data formats, and often operating across multiple OSI layers.
- ↑ https://en.wikipedia.org/wiki/Restrictions_on_geographic_data_in_China
- ↑ Dynamic DNS is another option for when your ISP changes your home network's IP address.It is a commercial service that allows you also to use a fixed address for your home network. You can often set up DDNS on your router. Self-hosted website or online resource will be redirected over commercial nodes maintained by companies; companies which are often known for data-exploitation, acts of censorship and compliance with states agencies in cases of political prosecution.
- ↑ Networks with an Attitude was a worksession to think of the future of Internet, organised by Constant from 7 to 13 April 2019 at various locations in Antwerp.The internet is dead, long live the internets! https://constantvzw.org/sponge/s/?u=https://www.constantvzw.org/site/-Networks-with-an-Attitude-.html
- ↑ Gray, Jonathan, Carolin Gerlitz, and Liliana Bounegru. “Data Infrastructure Literacy.” Big Data & Society 5, no. 2 (July 1, 2018) https://journals.sagepub.com/doi/10.1177/2053951718786316
- ↑ The documentation of this process https://zoiahorn.anarchaserver.org/physical-process/ is hosted on the anarchaserver. Anarchaserver is an allied feminist server which contributes to the maintenance of autonomous infrastructure on the Internet for feminists projects and was setup in Calafou, Spain.
- ↑ The fourteenth edition of the meeting days Verbindingen/Jonctions organized by constant vzw in December 2013 was dedicated to a Feminist review of mesh, cloud, autonomous, and DIY servers. https://areyoubeingserved.constantvzw.org/Summit.xhtml
- ↑ Goldjian and bolwerK started plotting the Cryptodance project during a Ministry of Hacking (hosted by esc in Graz, Austria), where they formed a joint(ad)venture of the Department of Waves and Shadow and the Department of Care and Wonder.Cryptodance - THF 2016
- ↑ Nate Wessalowski and xm developed it during 360 degrees of proximities for the cyborg collective of Caladona, a women center in Barcelona with whom they together installed peertube on a self-hosted server. ActivityPub provides a client-to-server API for creating and modifying content, as well as a federated server-to-server protocol for delivering notifications and content to other servers.
- ↑ Sollfrank, C."Forms of Ongoingness. Interview with Femke Snelting and spideralex". House for Electronic Arts (HeK), Basel. (September18, 2018) https://creatingcommons.zhdk.ch/wp-content/uploads/2020/06/Transcript-Femkespider.pdf
- ↑ spideralex in Sollfrank, C."Forms of Ongoingness. Interview with Femke Snelting and spideralex". House for Electronic Arts (HeK), Basel. (September18, 2018) https://creatingcommons.zhdk.ch/wp-content/uploads/2020/06/Transcript-Femkespider.pdf
- ↑ Gargaglione, E. “Hacking Maintenance With Care Reflections on the Self-administered Survival of Digital Solidarity Networks". Roots§Routes. (May 14, 2023). https://www.roots-routes.org/hacking-maintenance-with-care-reflections-on-the-self-administered-survival-of-digital-solidarity-networks-by-erica-gargaglione/ [client/server nor user/developper]
- ↑ Networks Of One’s Own is a periodic para-nodal publication by varia. September 2019. https://networksofonesown.varia.zone/
- ↑ Association for Progressive Communications.: Peña, P and Varon,J. “Consent to Our Data Bodies: Lessons From Feminist Theories to Enforce Data Protection,” oding Rights (March 25, 2019). https://www.apc.org/en/pubs/consent-our-data-bodies-lessons-feminist-theories-enforce-data-protection
- ↑ The Eclectic Tech Carnival (/ETC) is a potent gathering of feminists who critically explore and develop everyday skills and information technologies in the context of free software and open hardware. /ETC chews on the roots of control and domination, disrupts patriarchal societies and imagines better alternatives. https://monoskop.org/Eclectic_Tech_Carnival
- ↑ https://alexandria.anarchaserver.org/index.php/Main_Page#TransHackFeminist_Convergence
- ↑ Wessalowski, N. & Karagianni, M. “From Feminist Servers to Feminist Federation.” A Peer-Reviewed Journal About 12, no. 1 (September 7, 2023): 192–208. https://doi.org/10.7146/aprja.v12i1.140450
- ↑ Following a quote from Grace Lee Hoggs on connectedness and activism which puts 'critical connections' over 'critical mass' after an idea by Margaret Wheatly. Boggs, G., Kurashige, S. The Next American Revolution: Sustainable Activism for the Twenty-First Century. Univ of California Press, 2012. p.50)
- ↑ See also spideralex, referencing Remedios Zafra's book "A Connected Room of One’s Own" https://www.remedioszafra.net/aconnectedroom.html in Sollfrank, C."Forms of Ongoingness. Interview with Femke Snelting and spideralex". House for Electronic Arts (HeK), Basel. (September18, 2018) https://creatingcommons.zhdk.ch/wp-content/uploads/2020/06/Transcript-Femkespider.pdf
- ↑ Term introduced in this book by ooooo, which got picked up an lead to an in depth article on the subject in Chapter_5b:_Distribution
- ↑ Metahaven, Daniel van der Velden, and Vinca Kruk. 2012. ‘Captives of the Cloud: Part I’. E-Flux 37.