Coordinator: SysterServer with contributors: xm (ooooo), Mara and nate
intro
Online publics are not virtual or politically neutral 'cyberspaces', they result from the material and laborious networking of computers and 'the relations that form around them'.[3] The following text describes and documents some of the infrastructural practices around the Servpub project[4] which explores modes of 'making public' at the fringes of the locked-down publishing apparatus of the university. It also introduces and investigates the feminist principles of 'making space for ourselves*'[5] and 'choosing our* own dependencies'[6] which are tied to practices of networking, publishing and inhabiting online-offline spaces.
More concretely, this text recounts the collaborative modes of sharing infrastructures and responsabilities between Servpub und Systerserver. The collaboration (alliance?) is reflected on and documented by some of us Systerserver admins in exchange with other members of a further network of feminist servers and feminist sysadmins[7]. Both writing and publishing this text has been a recursive endeavor in the sense that it involved the infrastructures of the Servpub project resulting from the collaboration, such as the self-hosted wiki-to-print service. Furthermore the project relied on self-hosted services and organizational tools from Systerserver. Systerserver is one of the oldest feminist servers, founded in 2005 in the context of the Gender Changer Academy and the Ecelectic Tech Carnival.[8]

As part of Systerserver we are co-dependent on other feminist server projects (anarchaserver, Maadix, leverburns, digiticalcare...) and other autonomous tech collectives. Together we have a need to share ways of doing, tools & strategies to overcome/overthrow the monocultural, centralized oligopolic surveillance & technologies of control and We need to resist the matrix of domination. Stop the exploitation and continuation of social and climatological injustice(s)
We introduce and copy the tactics of Queercore: How To Punk A Revolution [9]. The documentary explores the rise of the queercore cultural and social movement in the mid-1980s, which channeled punk angst into a biting critique of societal homophobia. We introduce our feminist server's activities as a catalyst to push techno-feminism into existence and announce we are here to stay, even in the current tech-fascist oppressive society.
Mitigating dependencies (the problem and the 'research questions)
A server is a place where our data is hosted, the contents of our websites, where we are chatting, storing our stories and imaginaries and access the multiple online services we need to get organized (mailing lists, calendars, notes,...). We don't want to be served, we think a feminist server as an (online) space that we need to inhabit. As inhabitants, we contribute by nurturing a safe space and a place for creativity, experimentation and justice, a place for hacking hetero normative and patriarchal technologies. Feminist servers have the potential to learn, to maintain and care for a space together in a non-hierarchical way, and in a non-meritocratic way.
To be able to setup server's we need to have hardware, a machine - a single board computer (like raspberry pi, olimex, an old refurbished laptop/smartphone,...) or a server in a rack in a data center, a virtual machine (vps), and the will to self-host (described in chapter 1). As Systerserver, our feminist server project, we relate and organize around these servers by adopting different roles, defined in conversations with Anarchaserver's network.
Guardians are the people who report new updates, possible bugs [...] to ensure the security and the functionality of the services. They initiate collective meetings to address the issues and follow up that is gets done. Interfaces are people who are in-betweens to communicate about the feminist servers to our communities and allies. They also support the guardians by using the services and pointing out if some of them are not working or has issues. Scribes are the people who will be providing support by writing documentation during our collective meetings, either by creating content in our wiki, or in our gitlab, or by writing documents needed for their services, or by developing narratives. Fire extinguishers are the people who have the most experience, on who we can rely if we suffer an attack or something very strange is happening. They also guide while installing, configuring and debugging.
Besides from these roles we need to encourage “data infrastructure literacy” for the ability to account for, intervene around and participate in the wider socio-technical infrastructures in which data is created, stored and analyzed. Our intent is to make space for collective inquiry, experimentation, imagination and intervention around data. Data as in binary information, suitable for processing by computers, recognizing it's intrinsic (human)labour conditions, maintenance and hence care. In becoming more literate, we cultivate our sensibilities around data politics and as well engage a wider public with digital data infrastructures. [11]
For this reason we need to make servers visible and physical as a crucial/critical space, we need a room of our own and we need a ‘connected room’ of our own.* or a network of one's own [12] [13]
By making infrastructures visible with the aid of drawings, diagrams, manuals, metaphors, performances, gatherings, systerserver traverses technical knowledge with an aim to de-cloud (Hilfling Ritasdatter, Gansing, 2024) our data, and redistribute our networks of machines and humans/species.
A connected room, network of one's own, with allies as co-dependencies, attributes collectivities interacting as radical references which evades hierarchies of cognitive capital based on individuals and underlines the collective efforts to resist within the hegemonic technological paradigm. [14]
--

Public interface anarchaserver in calafou: https://zoiahorn.anarchaserver.org/physical-process/

Are you being served ? s performative event developed by ooooo which took place during The Feminist Server Summit, organized by constantvzw in brussels https://areyoubeingserved.constantvzw.org/Home_server.xhtml Home is a Server is about mimicking computer functioning through human energy and towards a human goal (eating the pancake instead of just publishing its recipe online), transforming ourselves into CPU, data, kernel, hard drive, booting, rebooting, getting into Kernel Panick and finally managing to get through the difficulties of sending data out, making a wiki that eventually achieves the very physical process of making pancakes for the group during the afternoon, 12–15 December 2013
politics of networks
Being part of the Internet, or internets, is a combination of vast, complex and opaque technologies we have to understand the technicalities of the Internet, such as IP address, Local, private and virtual networks, routing and subnetting and the politics of scarcity, economy and institutional control.
Systerserver has two physical machines in a data room in Graz @ mur.at, an association which enables the networking of a wide variety of art and cultural initiatives in a (shared) virtual space. Donna from the https://www.genderchangers.orgwent to install the most recent hardware in 20?? . The server is called Adele. The older machine we have since 20?? and is called Jean. Both are running a recent stable debian image with diverse services. Let's focus on Jean who hosts a mastodon and tinc[15]. Mastodon is a free and open-source software platform for microblogging and social networking. It operates within a federated network of independently managed servers that communicate using the ActivityPub protocol, allowing users to interact across different instances within the Fediverse. Tinc is a VPN tunneling software. It creates virtual private network(s), in which as as many servers can be added as preferred. The network is hidden, it only exists between the servers that are added to it, but it works with public entry points. So if a request is made to a server, it first connects to Jean server, which forwards the request internally, meaning inside the hidden network to the specific machine .[16]
In Jean, we configured three of these private networks, named "internes" and "alliances" and "systerserver". While the first is for our internal Systerserver network name to communicate with our backup server, the latter is for local servers from our community e.g the etherpad servers of leverburns which we use for documentation, ..... There is also the network named systerserver which was our first attempt to install and configure Tinc and makes the servers for this publication accessible. The servers that are connected to these networks are mostly home based with dynamic IPs that change. A home router switches the public IP regularly, they use what are called dynamic IP addresses, this means your public IP address change over time. This is because your internet service provider (ISP) temporarily assigns you an IP address from a pool. They do this to manage their available addresses more efficiently and for minor security benefits. So an ISP's lease time can expire which triggers an IP address change.
Hence for these servers to be accessible in the Internet they need a fixed (or static) IP. With the creation of the Tinc networks, servers can be accessed via the IP of jean which is a fixed IP. . Tinc (and other VPN) tunnels operate within private networks (10.0.0.0), and the machines 'invited' inside these tunnels can connect to each other. With reverse proxy, a configuration of your webserver (nginx, apache, ...), jean reroutes all the incoming and outgoing traffic to the servers that are part of the specific network(s).
The vpn-software + reverse proxy is a valuable strategy to avoid high costs for a static IP of your Internet Service Provider and to over come theshortage of IPv4. We have to keep in mind that adding new servers to our tinc network(s), creates more traffic and hence bandwidth use of the dataroom in [mur.at] .
choose your dependencies
An alternative for when your ISP changes your home network's IP address, would be Dynamic DNS, which is a useful service that allows you also to use a fixed and memorable address for your home network. You can often set up DDNS on your router. You can also run a DDNS client on one of your servers.
/// needs more... / generalisation + references
THIS SEEMS MORE INFORMATIVE /MAYBE IN SEORATE DESIGN STYLE
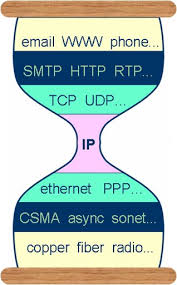
lan/wan/van
To understand somehow more the private and public IP’s and networks, we can look at them from their naming conventions. LAN is an abbreviation for LOCAL AREA NETWORK, and the reserved addresses for these networks are either 192.x.x.x, 169.x.x.x (DHCP) and 172.x.x.x. These addresses are distributed within one room, building that has a router. The router that broadcasts the WiFi or provides ethernet cable connections is the interface between the local network inside the room, and the WAN (WIDER ARE NETWORK), basically the Internet.
The addresses 10.x.x.x are reserved for the private networks, that are also called virtual. Since Virtual Private Networks are more complex to comprehend. Let's introduce a little bit of their history, hoping that it will illustrate their purposes and functions more.
regulatory bodies ICAN-RFC's develop/discuss standards (missing)
routing / subnetting (missing)
history and topology of VPN
After the WWW and http protocol, the question of secure connections became urgent as the ability to connect beyond institutional networks became wider. AT&T Bell Laboratories developed an IP Encryption Protocol (SwIPe), implementing encryption in the IP layer. This innovation had a significant influence on the development of IPsec, an encryption protocol that remains in widespread use today.
"IPsec, introduced around the mid-1990s, provided end-to-end security at the IP layer, authenticating and encrypting each IP packet in data traffic. Notably, IPsec was compatible with IPv4 and later incorporated as a core component of IPv6. This technology set the stage for modern VPN methodologies." [17]
By end of 90s Microsoft worked towards implementing a secure tunnel protocol, creating a virtual data tunnel to ensure more secure data transmission over the web. The encryption methods used in the PPPP was vulnerable to advanced cryptographic attacks. the MPPE (Microsoft Point-to-Point Encryption), only offers up to 128-bit keys which have been deemed insufficient for protecting against advanced threats. Later together with Cisco, they developed another protocol, the L2TP, for serving multiple types of internet traffic.
"L2TP (Layer 2 Tunneling Protocol) works by encapsulating data packets within a tunnel over a network. Since the protocol does not inherently encrypt data, it relies on IPsec (Internet Protocol Security) for confidentiality, integrity, and authentication of the data packets traversing the tunnel." [18]
A later tunneling protocol is the openVPN, which has been designed as a more flexible protocol allowing port configuration, and more security.
Tinc protocol follows here...
the drawing of encapsulation from tunnel up/down
While https is another way to secure traffic over the internet, it is distingue from IPSec in that IPsec secures all data traffic within an IP network, suitable for site-to-site connectivity. HTTPS, the secure version of HTTP, using SSL, and its successor TLS secures individual web sessions, typically used for secure remote access to specific applications via the internet.
geolocation and network infrastructures
Now that hopefully we have a clearer idea of the local/private networks vs the public networks aka Internet, it’s important to dive into the distribution of addresses and the politics that stem from this. According an online article about the state of the Internet as of 2023, several factors have contributed to the decline in IPv4:
• Market Saturation: The Internet may have reached a point where there is no additional demand to drive further growth, leading to a natural plateau in IPv4 usage.
• Shift to Content Distribution Networks (CDNs): The transition to CDNs for digital services has reduced the demand for traditional content distribution methods, impacting IPv4 growth.
• IPv4 Address Exhaustion: The depletion of available IPv4 addresses has led to the adoption of address-sharing technologies and significant architectural changes in Internet services, further contributing to the decline.
Despite these trends, the article notes that the majority of the Internet user base (slightly under two-thirds as of the end of 2022) still relies exclusively on IPv4. The future trajectory of IPv4 and IPv6 usage remains uncertain, influenced by technical developments, economic factors, and global events, such as pandemics, economic crises and communications technology in different parts of the word. IPv6 adoption is scant in most of Africa, the Middle East, Eastern and Southern Europe, and the western part of Latin America. Due to the market saturation and the smaller pace of network growth (double check) in those regions appears, for the moment, be adequately accommodated in the continued use of IPv4 NATs. This means that ISP can charge higher prices for a declined number of IPv4 and the need for self or community based hosting that relies on static and fixed IPv4s can be obtained through VPN tunnels and reverse proxies, or Tor onions. [19]
During the translation of the manuals Tunnel Up/ Tunnel Down, the Chinese artist and translator Biyi Wen pointed us to the art research project A Tour of Suspended Handshakes, in which artist Cheng Guo physically visits nodes of China’s Great Firewall. Using network diagnostic tools, he identifies the geolocations mapped to IP addresses of these critical gateways, based on data published by other researchers. At times, these geolocations correspond to scientific and academic centers, which seem like plausible sites for gateway infrastructure. Other times, they lead to desolate locations with no apparent technological presence. While Guo acknowledges that some gateways may be hidden or disguised—for example, antennas camouflaged as lamp posts—the primary reason for these discrepancies lies in the redistribution and subnetting of IP addresses, as well as their resale. These factors make it difficult to pinpoint exact geographical locations. Additionally, online IP location tools provide coordinates in the WGS-84 system (the global GPS standard), whereas locations in China must be converted to GCJ-02 (an encrypted Chinese standard). This further complicates geographic identification, as mapping activities have been illegal in mainland China since 2002. In the case of the Great Firewall, the combination of IP redistribution and encrypted coordinates obscures the true locations of its gateways, rendering the firewall a nebulous and elusive system. Similarly, for mobile (ambulant) servers, geolocating individual servers—beyond the main public-facing ones—remains a challenge. However, unlike the Great Firewall, the mobility of such servers is not enforced through top-down government control. This decentralization has the potential to counteract centralized policies and provide a means of circumvention. [20]
resources matter
traffic costs and electricity (missing)
index.php?title=Category:ServPub
- ↑ https://digitalcare.noho.st/pad/p/servpub
- ↑ https://eth.leverburns.blue/p/servpub-2b
- ↑ This infrastructural understanding of publishing and computer networks is indebted to Lauren Berlant, 2016. The commons: Infrastructures for troubling times*
- ↑ https://servpub.net/
- ↑ This is on one of the slides.
- ↑ After a formulation from the first Feminist Server manifesto: "A feminist server… is autonomous in the sense that she decides for her own dependencies." (https://areyoubeingserved.constantvzw.org/Summit_afterlife.xhtml)
- ↑ One important means for exchange and contact are emaillists, such as the adminsysters list hosted by Systerserver.
- ↑ More information about the /etc and past events see https://eclectictechcarnival.org/ET C2019/archive/.
- ↑ https://www.imdb.com/title/tt4643034
- ↑ https://creatingcommons.zhdk.ch/wp-content/uploads/2020/06/Transcript-Femkespider.pdf
- ↑ https://journals.sagepub.com/doi/10.1177/2053951718786316
- ↑ (Spideralex) https://creatingcommons.zhdk.ch/wp-content/uploads/2020/06/Transcript-Femkespider.pdf.
- ↑ referring to the paranodal periodic publication and series of events and worksessions in rotterdam revisting of Virgina Woolf's classic essay.
- ↑ https://www.roots-routes.org/hacking-maintenance-with-care-reflections-on-the-self-administered-survival-of-digital-solidarity-networks-by-erica-gargaglione/
- ↑ Genealogy - Mansoux developed the idea of the hub in the context of XPUB in 2019, enabling networked experiments and server related work to be done within the institution. The free software was used in the Traversal network of Feminist Server's project to make rosa, a mobile server accessible to the public internet
- ↑ https://atnofs.constantvzw.org/ATNOFS-screen.pdfp9
- ↑ https://www.paloaltonetworks.com/cyberpedia/history-of-vpn
- ↑ https://www.paloaltonetworks.com/cyberpedia/what-is-l2tp
- ↑ https://blog.apnic.net/2024/01/09/measuring-bgp-in-2023-have-we-reached-peak-ipv4/
- ↑ https://en.wikipedia.org/wiki/Restrictions_on_geographic_data_in_China